132 private links
Worried about the security of your Linux server? Learn some easy to implement tips on securing SSH and make your Linux server more secure.
Create a pdf with barcodes to backup text files on paper. Designed to backup ASCII-armored GnuPG and SSH key files and ciphertext.
Hashicorp Vault hogs the limelight as cost-effective powerful KMS solutions are hidden in plain sight. Chris McGrath explores the underrated Mozilla SOPS.
This HN thread contains several tips and hints regarding methods, approaches and tools to share secrets across people and systems.
How to SSH properly and easily improve the security of your SSH model without needing to deploy a new application or make any huge changes to UX.
SpicyPass is a light-weight password manager that utilizes state of the art cryptography and minimalist design principles for secure and simple password storage.
The firmware of microcontrollers usually contains valuable data such as intellectual property and, in some cases, even cryptographic material.

This guide explains how to edit remote files with Vim on Linux. Starting from Vim 7.x version, the netrw plugin allows you to edit remote system files.
The C language is still prominent in the industrial embedded world, where “IoT” often refers to platforms much more limited than a Raspberry Pi. Often having to deal with such environments, we wrote the following informal explainer about C for internal company needs, and thought it could be of interest for more readers. This is basic material, mixing C and operating systems knowledge, aimed at readers with no or limited understanding of how you go from C source code to an executable. We could expand on many points, but for now we just share this meandering overview.
Email is unsafe and cannot be made safe. The tools we have today to encrypt email are badly flawed. Even if those flaws were fixed, email would remain unsafe. Its problems cannot plausibly be mitigated. Avoid encrypted email.
Technologists hate this argument. Few of them specialize in cryptography or privacy, but all of them are interested in it, and many of them tinker with encrypted email tools.
Most email encryption on the Internet is performative, done as a status signal or show of solidarity.
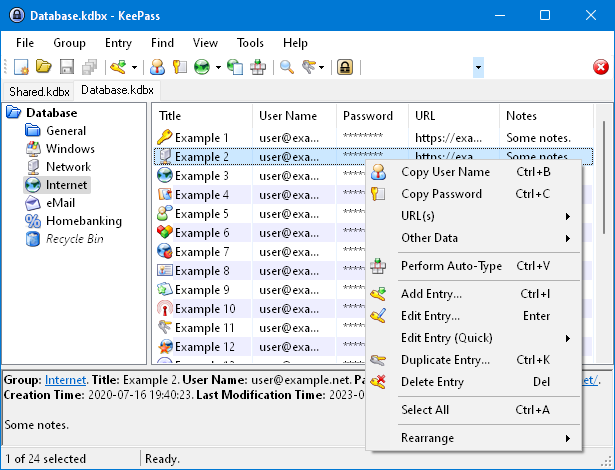
KeePass is a free open source password manager. Passwords can be stored in an encrypted database, which can be unlocked with one master key.
Bitwarden is a free and open source password management solution for individuals, teams, and business organizations.
Easy and safe way for individuals, teams, and business organizations to store, share, and sync sensitive data.
A command line interface (interactive shell) to work with KeePass 1.x or 2.x database files.

gopass is a rewrite of the pass password manager in Go with the aim of making it cross-platform and adding additional features. The target audience are professional developers and sysadmins (and especially teams of those) who are well versed with a command line interface.
In a world of evolving and targeted cyber threats understanding your attacker’s intentions and tools has never been more crucial. By deliberately maintaining vulnerable systems, or Honey Pots, and letting the attackers in you can analyse their activity and gather intelligence so you can be ahead of the game if you ever have a compromise. When running an SSH Honey Pot you can gain a full log of the commands an attacker attempts to run on your system and any files which they attempt to download and can be a great way to obtain samples of malicious software for analysis or understand the techniques used by an attacker to scour your data.
BusKill is a Kill Cord for your laptop implementing a Dead Man Switch using $20 in USB hardware + udev rule to trigger your laptop self-destruct if stolen.

Thirty years ago, Cliff Stoll published The Cuckoo's Egg, a book about his cat-and-mouse game with a KGB-sponsored hacker. Today, the internet is a far darker place—and Stoll has become a cybersecurity icon.
I read this book when I was young. Still remember the atmosphere :-)
