132 private links
Many of us use password managers to securely store our many unique passwords. A critical part of a password manager is the master password. This password protects all others, and in that way, it is a risk. Anyone who has it can pretend to be you… anywhere! Naturally, you keep your master password hard to guess, commit it to memory, and do all the other things you are supposed to do.

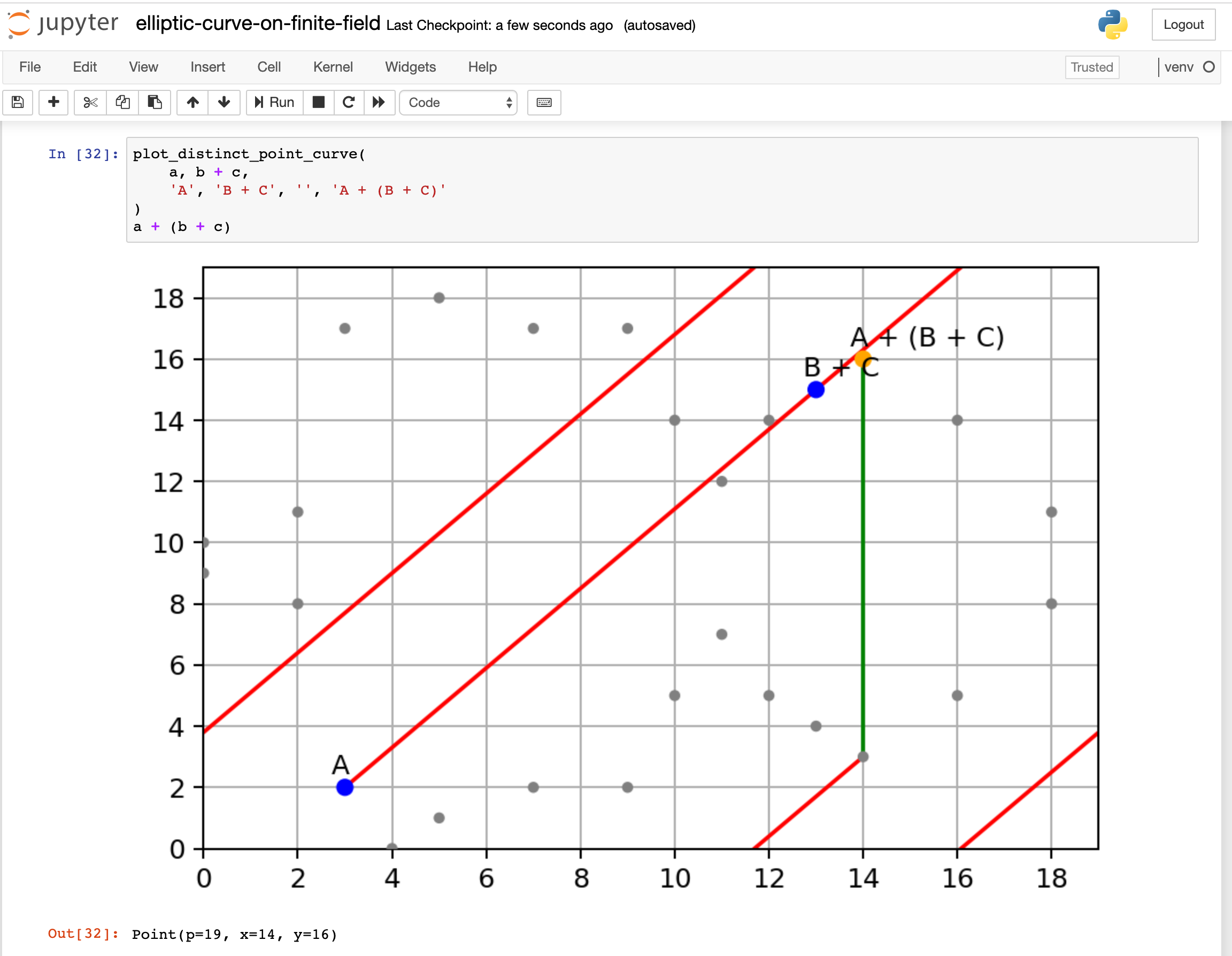
Recently, I am learning how Elliptic Curve Cryptography works. I searched around the internet, found so many articles and videos explaining it. Most of them are covering only a portion of it, some of them skip many critical steps how you get from here to there. In the end, I didn’t find an article that really explains it from end-to-end in an intuitive way.
With that in mind, I would like to write a post explaining Elliptic Curve Cryptography, cover from the basics to key exchange, encryption, and decryption.
At the heart of decentralized systems today is a demoralizing irony. Vast resources---intellect, equipment, and energy---go into avoiding centralized control and creating "trustless" systems like Bitcoin. But hapless users then defeat the whole purpose of these systems by handing over their private keys to centralized entities like Coinbase.
Would it be nice if there were a truly decentralized system that could do the impossible? I.e.,
- Make key management easier for ordinary users.
- Manage secret keys for transparent objects without secret state, like smart contracts.
- Operate seamlessly when nodes come and go.
A simulated Enigma machine, where the different parts of the machine are beautifully represented with graphics.
The notebook simulates an Enigma Machine and visualizes how it works. The Enigma Machine is an especially neat thing to visualize because it was electromechanical. As you used it, it moved. Instead of circuit traces, it had beautiful real wires connecting its pieces.
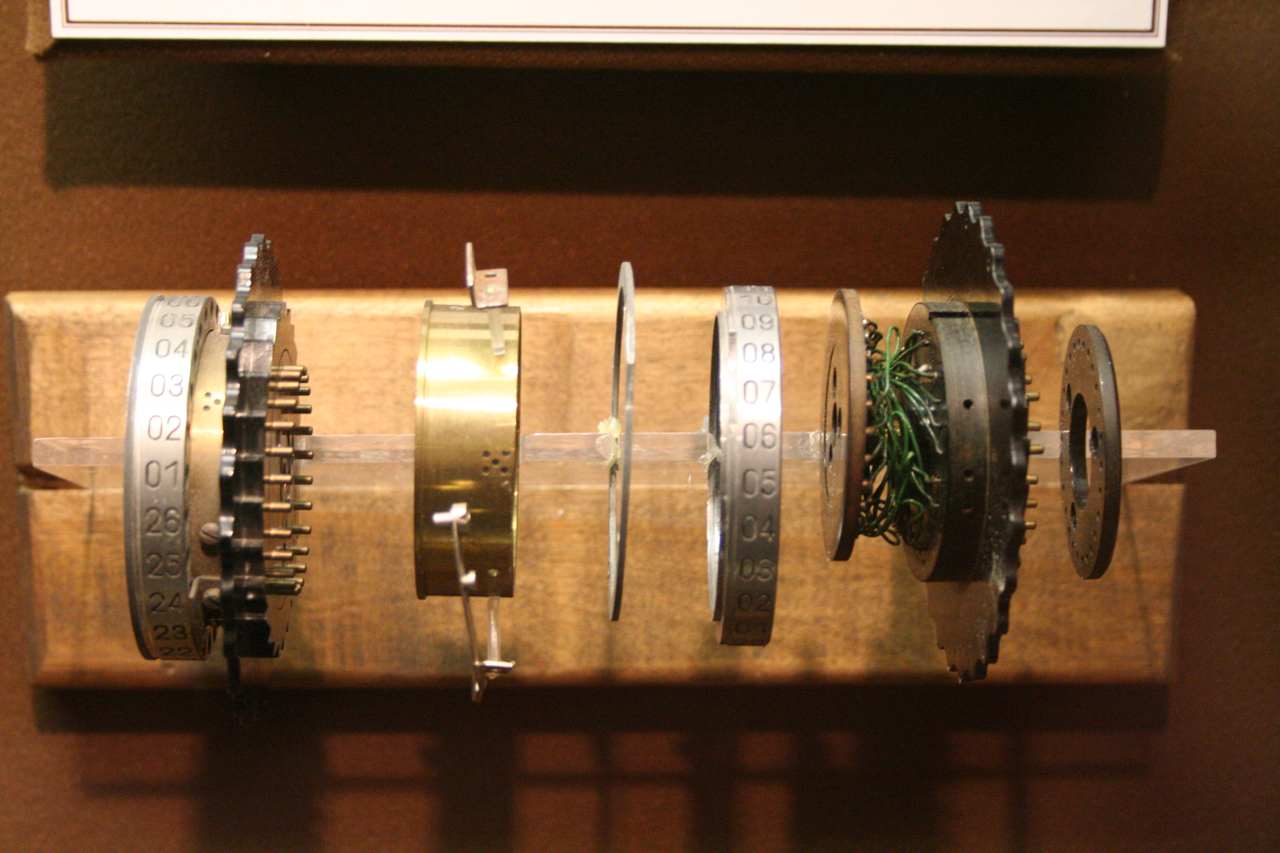
Image source: Wikipedia.
Steganography is the study and practice of concealing communication. It plays a different role to cryptography, with its own unique applications and strengths.

Signed/Encrypted ARchive: always-encrypted tar-like archive tool with optional signature support.
A History of Alice and Bob, by Quinn DuPont and Alana Cattapan (created 2017).

Tomb is an 100% free and open source system for file encryption on GNU/Linux. It simply makes gpg dm-crypt and cryptsetup usable in a variety of situations.
Written in bash.
We present HotStuff, a leader-based Byzantine fault-tolerant replication protocol for the partially synchronous model.
Once network communication becomes synchronous, HotStuff enables a correct leader to drive the protocol to consensus at the pace of actual (vs. maximum) network delay--a property called responsiveness--and with communication complexity that is linear in the number of replicas. To our knowledge, HotStuff is the first partially synchronous BFT replication protocol exhibiting these combined properties. HotStuff is built around a novel framework that forms a bridge between classical BFT foundations and blockchains. It allows the expression of other known protocols (DLS, PBFT, Tendermint, Casper), and ours, in a common framework.
Our deployment of HotStuff over a network with over 100 replicas achieves throughput and latency comparable to that of BFT-SMaRt, while enjoying linear communication footprint during leader failover (vs. quadratic with BFT-SMaRt).
A simple shell utility for encrypting and decrypting files.
Looking for a quick, easy, and secure method to protect your files? Well, there is a simple shell utility called “Cryptr” that helps you to encrypt and decrypt files. All from command line, and you...
This tutorial shows how to use eCryptfs to encrypt a directory on Ubuntu 16.04. eCryptfs is a POSIX-compliant enterprise-class stacked cryptographic f...
zbackup is a globally-deduplicating backup tool, based on the ideas found in rsync. Feed a large .tar into it, and it will store duplicate regions of it only once, then compress and optionally encrypt the result. Feed another .tar file, and it will also re-use any data found in any previous backups. This way only new changes are stored, and as long as the files are not very different, the amount of storage required is very low. Any of the backup files stored previously can be read back in full at any time. The program is format-agnostic, so you can feed virtually any files to it.
This is achieved by sliding a window with a rolling hash over the input at a byte granularity and checking whether the block in focus was ever met already. If a rolling hash matches, an additional full cryptographic hash is calculated to ensure the block is indeed the same. The deduplication happens then.
To process a transaction, you need first to make sure the sender owns the asset he wants to transfer, and make sure he will not trade it twice.
In the blockchain, information is stored in blocks that record all transactions ever done through the network. Hence, it allows validating both the existence of assets to be traded and ownership.
To avoid double spending, the technology requests several nodes to agree on a transaction to process it. A validation is also artificially difficult to achieve: miners leverage computer power to solve complex cryptographic problems (the proof-of-work). Every time a problem is cracked, a block is added to the chain, and all the transactions it includes are thus validated. The updated chain, including the new block, is shared with other nodes and becomes the new reference; this process leverages cryptography to prevent duplicate transactions.
If you're a web developer, you've probably had to make a user account system. The most important aspect of a user account system is how user passwords are protected. User account databases are hacked frequently, so you absolutely must do something to protect your users' passwords if your website is ever breached. The best way to protect passwords is to employ salted password hashing. This page will explain why it's done the way it is.
There are a lot of conflicting ideas and misconceptions on how to do password hashing properly, probably due to the abundance of misinformation on the web. Password hashing is one of those things that's so simple, but yet so many people get wrong. With this page, I hope to explain not only the correct way to do it, but why it should be done that way.
