Daily Shaarli
10/09/19
If you already don’t want to talk to your kids about sex, then it’s probably a safe bet that you really don’t want to talk to them about pornography. But with how easily accessible porn is on the internet and the prevalence of computers, tablets and smartphones in the hands of our kids (or their friends), they will almost certainly stumble upon it at some point—and probably at a much younger age than you’d expect.
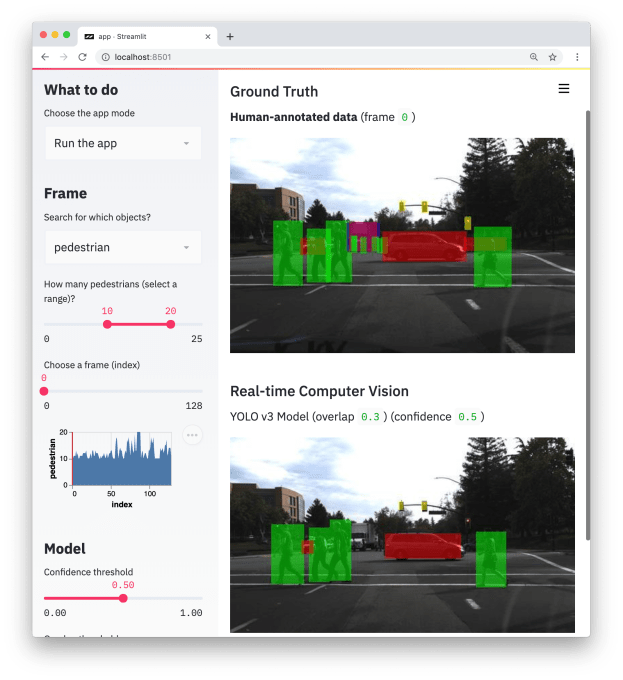
Introducing Streamlit, an app framework built for ML engineers.
The best designers employ specific habits, learned practices, and observed principles when they work. Here are a few of them.
- Experts involve the user
- Experts design elegant abstractions
- Experts focus on the essence
- Experts simulate continually
- Experts look around
- Experts reshape the problem space
- Experts see error as opportunity
- Experts think about what they are not designing
(read the article: nice pictures to visualize the different concepts :-))
Somewhere around 2014 I found an /etc/passwd file in some dumps of the BSD 3 source tree, containing passwords of all the old timers such as Dennis Ritchie, Ken Thompson, Brian W. Kernighan, Steve Bourne and Bill Joy.
Perché niente è impossibile da capire… Se lo spieghi bene !
PCA is a linear dimensionality reduction technique. Many non-linear dimensionality reduction techniques exist, but linear methods are more mature, if more limited.
Streamlit is the first app framework specifically for Machine Learning and Data Science teams.
So you can stop spending time on frontend development and get back to what you do best.
I often advocate people surrounding me to build their own side projects. I believe they can fulfill you in so many ways: for your career, your relationships, or your independence. Buffer, the company I currently work for, was itself a side project.
I’ve built myself multiple side projects. The major ones being PartyInBeijing (inactive), Nodablock (inactive), Citymayor (need to fix), and now TravelHustlers. I believe each of them contributed and lead me to my current situation: being satisfied in my career, financially, and socially.
JSON manipulation and transformation tool. Contribute to ldn-softdev/jtc development by creating an account on GitHub.
Keyword extraction (also known as keyword detection or keyword analysis) is a text analysis technique that consists of automatically extracting the most important words and expressions in a text.
It helps summarize the content of a text and recognize the main topics which are being discussed.
The AppSync Serverless Component allows you to easily and quickly deploy GraphQL APIs on AWS, and integrate them with AWS Lambda, DynamoDB & others.
It supports all AWS AppSync features, while offering sane defaults that makes working with AppSync a lot easier without compromising on flexibility.
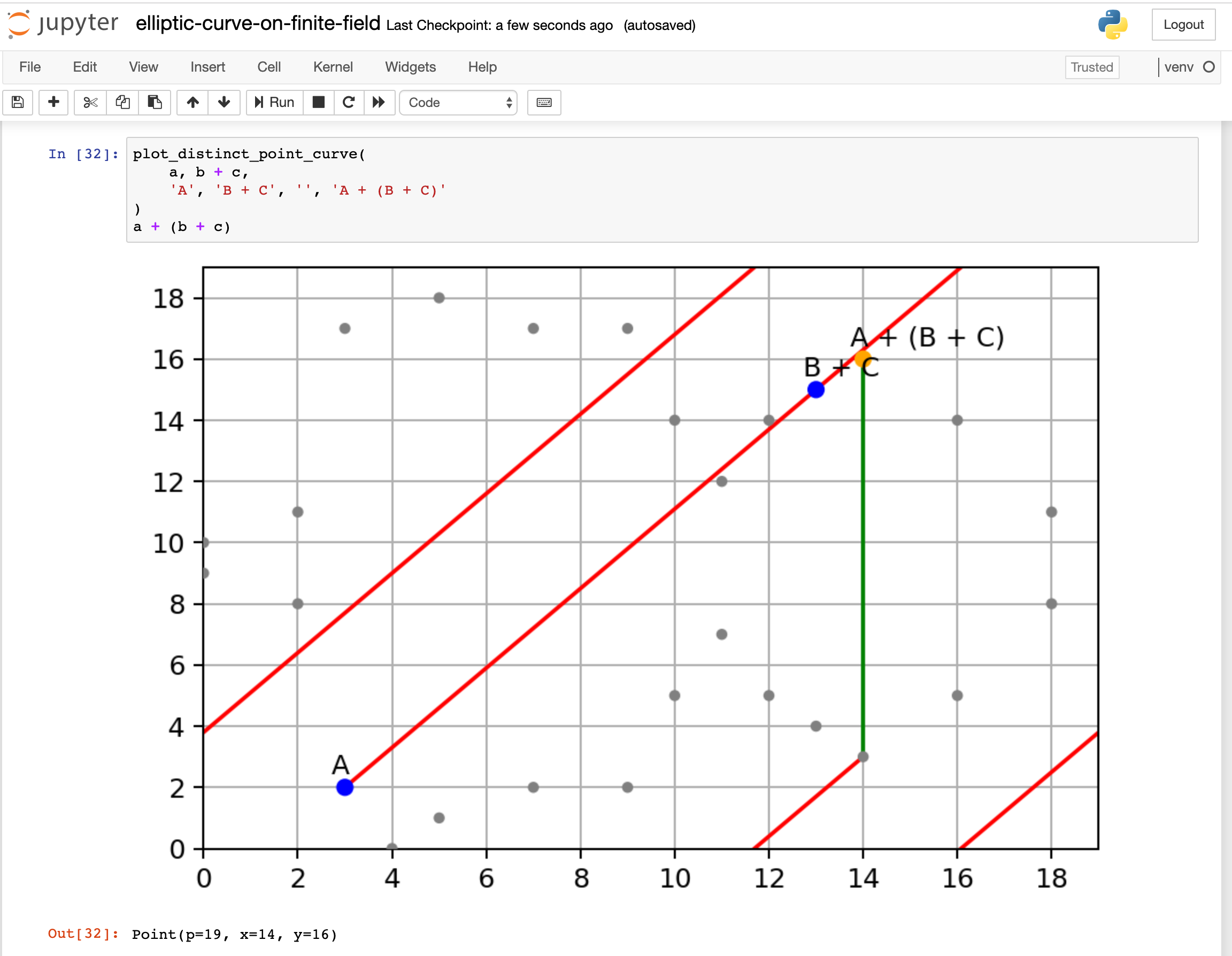
Recently, I am learning how Elliptic Curve Cryptography works. I searched around the internet, found so many articles and videos explaining it. Most of them are covering only a portion of it, some of them skip many critical steps how you get from here to there. In the end, I didn’t find an article that really explains it from end-to-end in an intuitive way.
With that in mind, I would like to write a post explaining Elliptic Curve Cryptography, cover from the basics to key exchange, encryption, and decryption.
AI research is making great strides toward its long-term goal of human-level or superhuman intelligent machines. If it succeeds in its current form, however, that could well be catastrophic for the human race. The reason is that the “standard model” of AI requires machines to pursue a fixed objective specified by humans.
We are unable to specify the objective completely and correctly, nor can we anticipate or prevent the harms that machines pursuing an incorrect objective will create when operating on a global scale with superhuman capabilities. Already, we see examples such as social-media algorithms that learn to optimize click-through by manipulating human preferences, with disastrous consequences for democratic systems.